How to apply your company user naming convention on Hashicorp Vault
Our world is using more and more digital services every day. A vast majority of modern systems are relying on databases to store various kind of sensitive information, from health metrics to financial reports for example. One of the biggest challenge nowadays lies to the security of this data, and especially talking about access control, as threats may came both from inside the company and also outside.
In this article, we will see how companies can apply their user naming convention to dynamic access managed by Hashicorp Vault, allowing a better audibility of users access.
Vault is can be used with a myriad of secret engines, here's the list of them supporting the username templating feature:
| Secret Engine name | Vault minimal version |
|---|---|
| PostgreSQL | Vault 1.7 |
| LDAP | Vault 1.7 |
| MySQL/MariaDB | Vault 1.7 |
| MSSQL | Vault 1.7 |
| MongoDB | Vault 1.7 |
| Couchbase | Vault 1.7 |
| Cassandra | Vault 1.7 |
| RabbitMQ | Vault 1.8 |
| SnowflakeDB | Vault 1.8 |
| RedShift | Vault 1.8 |
| MongoDB Atlas | Vault 1.8 |
| InfluxDB | Vault 1.8 |
| Elasticsearch | Vault 1.8 |
By default, the database secrets engines generate usernames using a default pattern. Here's a preview:
v-token-readonly-wGLPkpDyc6AgqBfMZTD3-1604195404
One should strongly consider managing their Vault cluster using infrastructure as code. Accordingly, the following steps will use Terraform and the Terraform Vault provider.
Considering the following configuration:
resource "vault_mount" "acme_research_database" {
path = "acme/research"
type = "database"
}
resource "vault_database_secret_backend_connection" "production" {
backend = vault_mount.acme_research_database.path
name = "production"
verify_connection = true
allowed_roles = (redacted)
postgresql {
connection_url = (redacted)
max_open_connections = (redacted)
username = (redacted)
password = (redacted)
}
}
The following naming convention should be used at "Acme" company:
[role]-[user]-[uuid]
Using username templating functions, this result to:
{{.RoleName | replace \"_\" \"-\" }}-{{.DisplayName}}-{{uuid | truncate 6}}
Now, update the Terraform configuration to apply this convention to the Postgres backend connection:
resource "vault_mount" "acme_research_database" {
path = "acme/research"
type = "database"
}
resource "vault_database_secret_backend_connection" "production" {
backend = vault_mount.acme_research_database.path
name = "production"
verify_connection = true
allowed_roles = (redacted)
postgresql {
connection_url = (redacted)
max_open_connections = (redacted)
username = (redacted)
password = (redacted)
username_template = "{{.RoleName | replace \"_\" \"-\" }}-{{.DisplayName}}-{{uuid | truncate 6}}"
}
}
Here's the result:
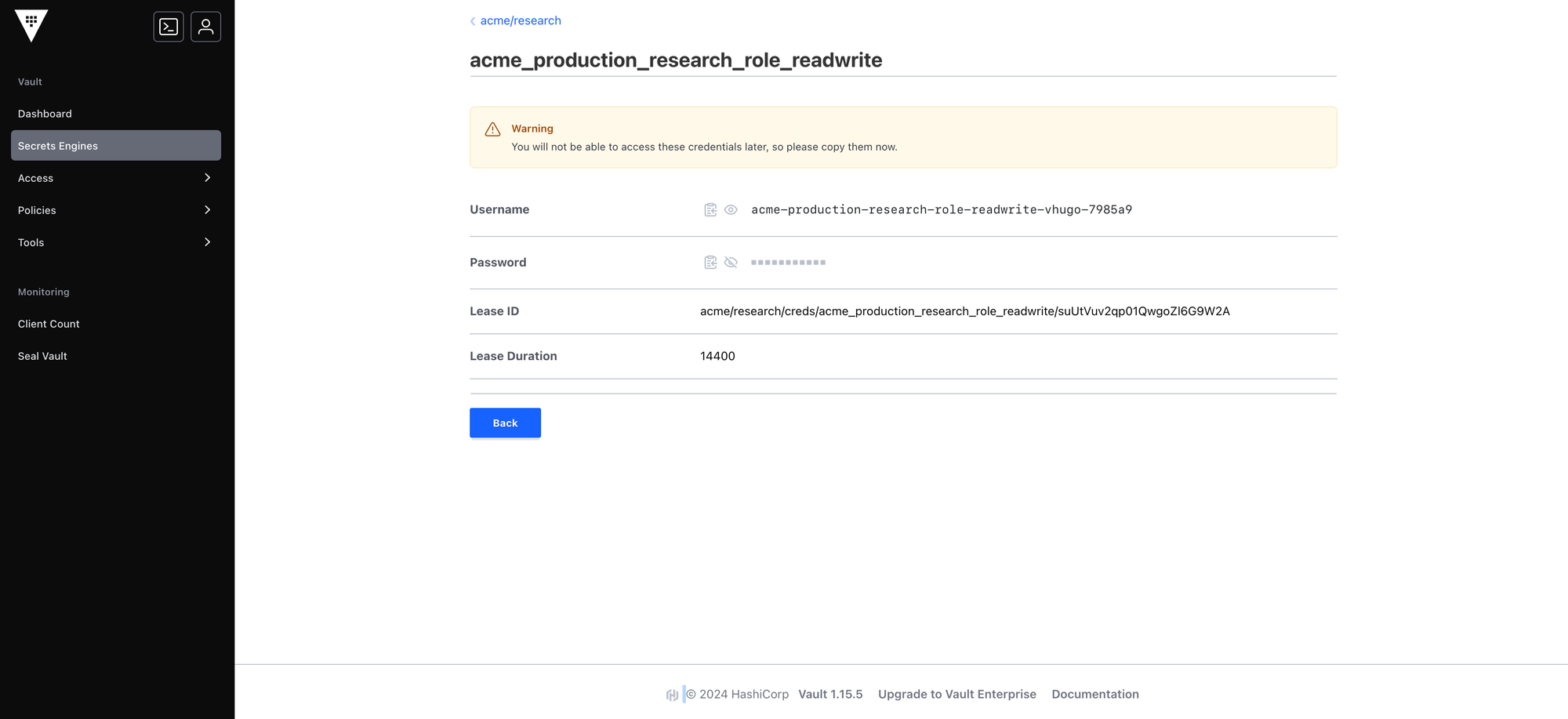
You have successfully applied the naming convention!
Links

Lenstra helps companies leverage Computer Science to enhance their Economic Performance
Contact us for a free consultancy to explore how we can work together.
Contact us