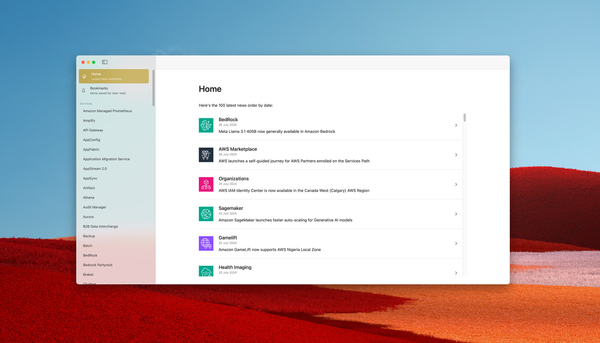
How to apply your company password policy convention on Hashicorp Vault
In a recent post, we've seen how your user naming convention can be applied to some of the dynamic secrets Vault can handle.
In this article, we will see how companies can also set their password policy convention.
Policy creation
The password policy is a simple JSON or HCL file which defines rules to match for the password to be generated. Here's a password policy sample:
length = 30
rule "charset" {
charset = "abcdefghijklmnopqrstuvwxyz"
min-chars = 1
}
rule "charset" {
charset = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
min-chars = 5
}
rule "charset" {
charset = "0123456789"
min-chars = 2
}
rule "charset" {
charset = "!@#$%^&*"
min-chars = 10
}Policy rollout
One should strongly consider managing their Vault cluster using infrastructure as code. Accordingly, the following steps will use Terraform and the Terraform Vault provider:
resource "vault_password_policy" "confidential" {
name = "confidential"
policy = <<EOT
length = 30
rule "charset" {
charset = "abcdefghijklmnopqrstuvwxyz"
min-chars = 1
}
rule "charset" {
charset = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
min-chars = 5
}
rule "charset" {
charset = "0123456789"
min-chars = 2
}
rule "charset" {
charset = "!@#$%^&*"
min-chars = 10
}
EOT
}
resource "vault_password_policy" "secret" {
name = "secret"
policy = <<EOT
length = 100
rule "charset" {
charset = "abcdefghijklmnopqrstuvwxyz"
min-chars = 1
}
rule "charset" {
charset = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
min-chars = 10
}
rule "charset" {
charset = "0123456789"
min-chars = 10
}
rule "charset" {
charset = "!@#$%^&*"
min-chars = 20
}
EOT
}
resource "null_resource" "apply_password_policy" {
triggers = {
policy_name = vault_password_policy.secret.name
}
provisioner "local-exec" {
command = <<-EOF
curl --silent --insecure --header "X-Vault-Token: $VAULT_TOKEN" --request POST --data '{"password_policy":"${vault_password_policy.secret.name}"}' "$VAULT_ADDR/v1/${vault_mount.mysql.path}/config/${vault_database_secret_backend_connection.cluster.name}"
EOF
}
}Links

Lenstra helps companies leverage Computer Science to enhance their Economic Performance
Contact us for a free consultancy to explore how we can work together.
Contact us